What Are The Best Practices For App Authentication?
Rohan Roy
Mar 7, 2025
App Development






Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?
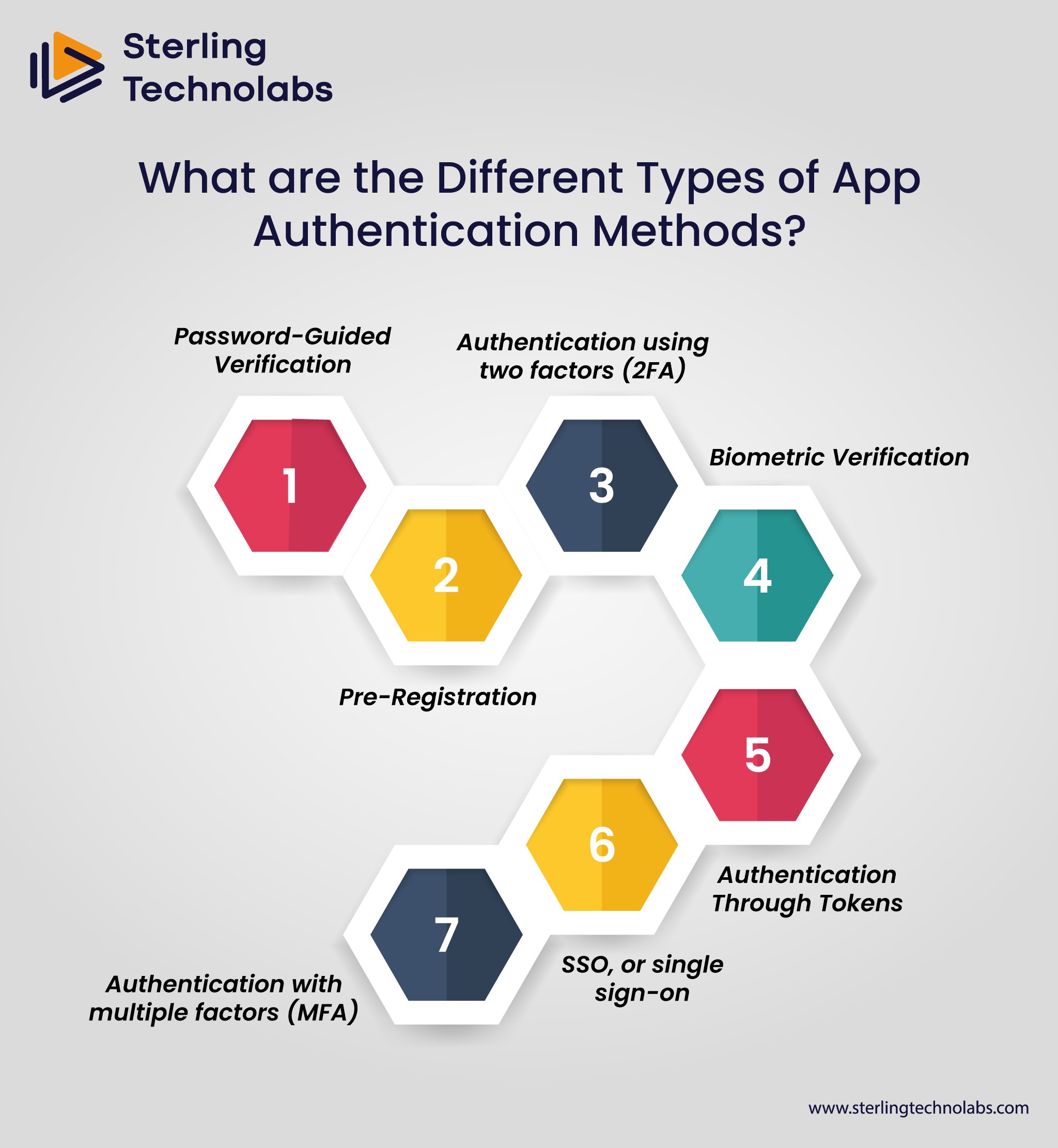
Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?

Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?

Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?

Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?

Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Passwords, biometrics, PINs, one-time codes, social login, and third-party services are some of the several methods you can use for App Authentication users in your mobile app. Depending on the functionality, target audience, and context of your app, each approach offers pros and cons of its own. The approach that best fits your app's development resources, user expectations, and security requirements should be selected.
For instance, biometrics may provide a high degree of convenience and App Security, but they might not function well for users with disabilities or in loud or low-light conditions. Passwords can be simple to create, but they can also be simple to forget, misplace, or compromise.
It can be difficult to choose the best user authentication method for your mobile application. You usually start with what you know best when considering best practices and tactics for mobile app authentication: user authentication to online applications.
The various authentication techniques that developers might employ to guarantee user data security will be examined in this article. This guide will therefore assist both developers and users in making well-informed decisions on app security. Continue reading to find out more.
Understanding What is Authentication?
Verifying the identity of a user or device trying to access a system or application is known as App Authentication. It's a basic security feature that guarantees sensitive data can only be accessed by authorized individuals.
Usually, users must provide their login information, including their username and password, in order to access mobile and web applications. These credentials are subsequently sent to a server by the app for validation. If the credentials match what is on file, you can access the features and functions of the app.
From straightforward username and Password Security combinations to multifactor authentication, authentication can take many different shapes. The security level of the app and the sensitive information the user wants to access determine the authentication method.
What are the Different Types of App Authentication Methods?

Password-Guided Verification
Passwords are the most often used authentication technique. A person's password could be made up of special characters, numbers, or letters. To guarantee robust security, you should make strong passwords with a variety of options.
Authentication using two factors (2FA)
By forcing the user to submit a one-time code, it strengthens password-based authentication. For instance, it is improbable that someone who guessed your password would also get the one-time code that was sent to your device. This may cause more trouble for consumers, but it also makes it more difficult for hackers to obtain unauthorized access.
Biometric Verification
Biometric Authentication confirms a person's identity by using distinctive behavioral or physical characteristics. It is being utilized more and more in a variety of industries, such as security, healthcare, and banking, to lower the risk of fraud and identity theft. Each of the numerous biometric authentication techniques has advantages and disadvantages.
Authentication Through Tokens
Token-based authentication verifies users and allows access to an application using a token or digital signature. It removes the need for passwords in web apps and APIs and offers improved security.
Users can provide their login information using token-based authentication, and the server will validate it. Upon successful authentication, the client receives a token from the server. In order to access protected resources, the client then provides this token in all ensuing requests to the server. The server verifies the token each time a request is received and, if it is legitimate, allows access.
SSO, or single sign-on
With just one login, users can access numerous apps and systems thanks to the single sign-on (SSO) technique. This method enhances the user experience and expedites the authentication process while preserving a high level of security.
Without having to enter their login information again, SSO enables users to authenticate once and then access all authorized apps and services. In business settings where users must access numerous apps and systems, it is frequently used.
Authentication with multiple factors (MFA)
Two or more user identification techniques are needed for the Multi-Factor Authentication (MFA) methodology. Face recognition, voice biometrics, fingerprints, Captcha puzzles, and smartphone codes are a few examples.
Because MFA authentication techniques and technologies give additional layers of security, users feel more secure. MFA has disadvantages even though it might be a good defense against the majority of account hacks. An authentication code cannot be generated if a person loses their phone or SIM card.
Why is App Authentication Important?
The user enters their login information, including their username and password, via a conventional authentication procedure. Either on an authentication server or in the local operating system, the user directory is queried by the authentication system. The user can access the system if their credentials match. The second step involves assigning people permissions that dictate which objects or processes they may access, along with other access privileges like rate restrictions and permitted access times. Here is importance of App Authentication:
Protecting sensitive systems and data: Authentication makes sure that only people with permission can access these resources. This is essential for safeguarding company assets from potential breaches and illegal access.
User accountability: Authentication systems keep track of user activity by confirming users' identities. This makes it possible for businesses to trace actions back to certain users, which is crucial for audit trails and regulatory compliance.
Facilitating safe remote work: As remote work becomes more popular, authentication is essential for protecting remote access to company networks and software. It guarantees that remote workers from different places can securely access company resources.
Identity and Access Management (IAM) support: An essential part of IAM systems, which control user identities and resource access, is authentication. By guaranteeing that users have access to only the resources required for their jobs, this upholds the principle of least privilege.
Improving the user experience: Single sign-on (SSO) and biometric authentication are two examples of contemporary authentication techniques that simplify user access to numerous apps and services. This increases user convenience and security overall and eliminates the need for numerous passwords.
Protecting sensitive transactions: Authentication lowers the risk of fraud and ensures data integrity in industries that handle sensitive transactions, such as financial services and healthcare.
What are the Best Practices of App Authentication?
The following are the Best Practices for App User Authentication:
Simplify the Process of Authentication
Because complex authentication can lead to user annoyance and desertion, simplicity is essential. Single sign-on (SSO), for instance, makes things easier by enabling users to access numerous apps using their current login credentials. Using a password manager that creates complicated passwords and logs people in automatically is an additional choice.
Provide a Variety of Authentication Choices
Providing a variety of authentication choices helps accommodate varying user preferences. While some prefer an OTP, others prefer biometric authentication, such as fingerprint scanning. Users can select the choice that best suits their needs from a variety of options.
Put Error Handling into Practice
Error handling should be used to enhance user experience and lessen user annoyance. The system ought to provide users with unambiguous feedback about what went wrong if they provide incorrect login information. The system should also guard against locking users out after an excessive number of unsuccessful login attempts.
Make Use of Simple and Direct Wording
To make sure users comprehend the authentication procedure, it's critical to utilize terminology that is straightforward and simple. Avoid using complicated terminology or technical jargon that users could find difficult to understand. Give users clear instructions to help them understand what they need to do during authentication.
Facilitate User Password Resets
By giving consumers a simple and fast mechanism to reset their passwords, you can keep them from becoming annoyed. This can involve choices like utilizing a security question or sending a password reset email.
Examine the process of authentication.
Testing the authentication procedure is crucial to fully identifying any potential issues. You can use tests to gather customer input and adjust your product accordingly. Additionally, analytical tools can offer insightful information about how users engage with authentication procedures and areas for development.
Make Your Work More Accessible
To make the login procedure accessible to visually impaired users, provide graphics with high contrast colors or alternate language.
What are Possible Future Trends of Authentication?
The following are the possible Future Trends in App Authentication:
By offering future predictive security measures, AI has the potential to completely transform authentication. AI enables authentication systems to identify questionable activity and stop security risks before they become an issue.
They can instead utilize their fingerprints, which are a more natural and straightforward form of authentication. In the upcoming years, we should anticipate that more businesses will use biometrics and token-based authentication techniques.
The user experience is more convenient when password control is removed. Users are no longer concerned about forgetting complicated passwords or having to remember them. As an alternative, they can employ a more intuitive and natural identification technique, such face or fingerprint recognition.
Alternative authentication techniques, which are more user-friendly and safe, are replacing password policies. These include risk-based authentication, biometrics, and tokens, which use behavioral analysis and machine learning to identify and stop fraudulent activity.
Conclusion
Protecting user data is crucial in the current digital era, as identity theft and data breaches are becoming more common. Therefore, the adoption and security of your app can be greatly impacted by the choice of authentication technique.
Keep a close eye on and record every authentication attempt so you can identify and address any questionable activity. Put in place thorough logging procedures that record information such IP addresses, user-agent strings, and login times.
App developers can utilize a range of authentication techniques, from contemporary biometrics to more conventional usernames and passwords. However, the optimal authentication technique depends on a number of criteria, including security, user experience, and legal compliance.

FAQs
Q: What are the most effective authentication methods for mobile and web applications?
A: As mentioned above biometric authentication, SSO authentication, password verification, two factor authentication, token authentication, and multiple factor authentication are the effective ways.
Q: How does two-factor authentication (2FA) enhance app security?
A: It combines a one-time password (OTP) or another type of identification with a login and password. OTPs are frequently sent by phone call or text message.
Q: What are the benefits and limitations of biometric authentication in apps?
A: An easy and safe method of user authentication in apps is biometric authentication. Sensitive information must be captured and stored for biometric authentication to work; otherwise, it may result in false positives or employ stolen biometrics.
Q: How can we ensure our app's authentication process provides a seamless user experience?
A: Don't include more than what is required to create an account. Regularly conduct training sessions that incorporate phishing and other typical attack simulations. Users will be better able to identify and address threats thanks to this. Test and update your authentication system on a regular basis.
Q: What are the common pitfalls to avoid when implementing authentication in applications?
A: Passwords that are too short may become less secure. It is simpler for attackers to guess passwords that are short or widely used. The system becomes susceptible to hacks and attacks if users are permitted to continue using the default passwords.
Recent Posts
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India
Ai
Services
Technologies
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India
Ai
Services
Technologies
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India
Technologies
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India
Ai
Services
Technologies
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India
Ai
Services
Technologies
Transform your vision into reality with Custom Software Development
Get Started
Office Address:
743A, Gera’s Imperium Rise,Hinjewadi Phase II, Rajiv Gandhi Infotech Park, Near Wipro Circle, Pune- 411057, Maharashtra, India






